

The blockchain ecosystem is a complex network of computational protocols and cryptographic techniques that enable a secure, distributed ledger of transactions.
At its core, blockchain technology is designed to provide a decentralized platform for various applications, from financial exchanges to contract management, without the need for a central authority.
The integrity and functionality of these networks heavily rely on transaction fees. They serve as both a reward mechanism for network validators and a deterrent against spam transactions.
What is the shift to self-custody all about and where does it push the advancement of the blockchain ecosystem? Keep reading to find out.
Blockchain networks operate on the principle of consensus, ensuring all participants agree on the state of the ledger. Participants in the network, also referred to as miners or validators, carry out tasks like transaction validation and block creation to achieve this.
These actors require compensation for their computational efforts and the resources expended in the process.
This is where fees come in. Fees are a critical component in this equation, often varying based on network demand, transaction complexity, and the underlying economic models of each blockchain.
Transaction fees aren’t just a source of income for network maintainers; they also play a pivotal role in network security.

By imposing a cost on transactions, blockchains inherently reduce the risk of malicious actors flooding the network with insignificant or harmful transactions, which could otherwise lead to network congestion or even attacks such as Distributed Denial of Service (DDoS).
Recent changes in the industry have significantly altered the blockchain narrative, underscoring the proverb "not your keys, not your coins."
The collapse of centralized entities like FTX and Celsius has cast a stark light on the vulnerabilities inherent in third-party custody. These incidents have triggered a seismic shift towards self-custody, where users maintain direct control over their private keys — and therefore, their assets.
This pivot isn’t just a reactionary step, but a return to the foundational principles of blockchain technology: decentralization and self-sovereignty.
The surge in hardware and software wallet adoption after these events shows the growing recognition of self-custody. Industry giants in the wallet market have reported unprecedented growth, demonstrating a collective move towards asset management solutions that empower users with full control.
During this shift, the wallet infrastructure's role has evolved from simple asset storage to a comprehensive asset management solution.
Crypto wallets are now expected to provide an interface for the complex interactions users have with various blockchain applications. They're not just gatekeepers of digital assets but facilitators of a broader economic activity within the blockchain space.
The contemporary wallet infrastructure has to balance a trifecta of demands:
As users seek greater control over their assets, the wallet becomes the nexus of their blockchain experience. The wallet's architecture dictates not only the safety of the assets but also the user's ability to interact with decentralized applications (dApps), participate in blockchain governance, and execute transactions.
The rise of new wallet models, such as smart contract wallets and those based on multi-party computation (MPC), represents the industry's response to the growing need for more sophisticated asset management tools.
These solutions aim to mitigate the risks associated with traditional wallets, such as single points of failure, while providing more granular control over transaction processes and improved recovery mechanisms.
In essence, the wallet infrastructure is the foundation upon which the promise of a decentralized financial system is built.
It’s the interface that translates the intricacies of blockchain technology into actionable, secure, and user-friendly applications.
As the blockchain ecosystem continues to expand and diversify, the evolution of wallet infrastructure remains critical, ensuring that the principles of self-custody and user empowerment remain at the forefront of the industry's progression.
The blockchain industry is undergoing a profound transformation from reliance on centralized entities to a staunch belief in the ethos of self-custody.
This paradigm shift is not an abrupt change but a gradual awakening sparked by a series of incidents that exposed the frailties of centralized trust.
Centralized platforms have long been the custodians of user assets, offering convenience at the cost of control. However, a spate of security breaches, mismanagement, and outright fraud have shattered the illusion of safety these entities promised.
Notable incidents include the fall of once-trusted exchanges like FTX and the liquidity crises of lending platforms such as Celsius. These events served as a wake-up call, illustrating the perils of entrusting assets to third-party intermediaries.
In the wake of these calamities, hardware and software wallets have seen a meteoric rise in popularity. Users have turned to solutions like Ledger and Trezor for hardware security and MetaMask and Trust Wallet for software-based asset management.
These tools empower individuals with complete control over their private keys — the cryptographic equivalent of a bank account password. However, it comes with no possibility of a password reset or a central authority's intervention for recovery.
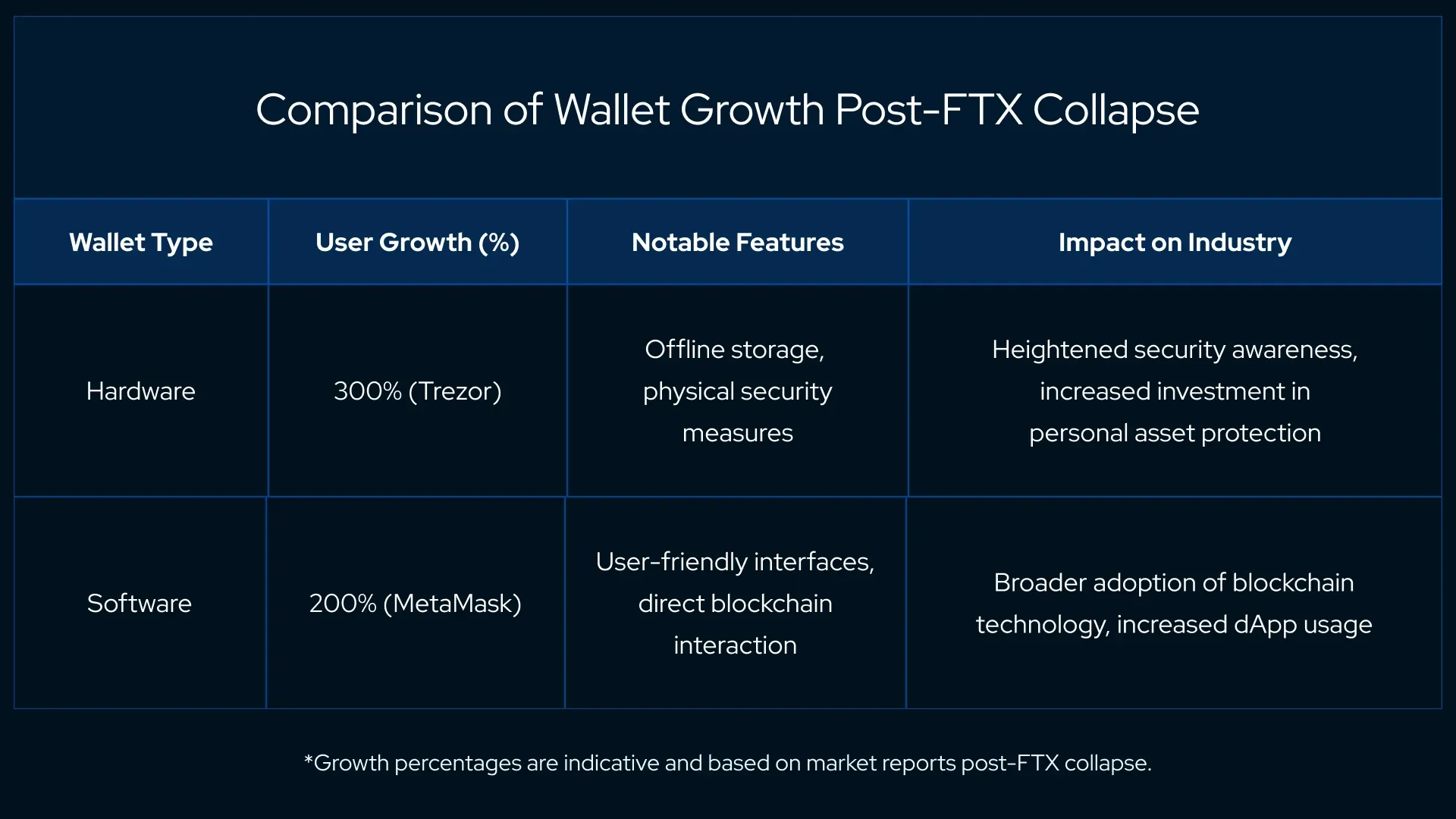
The industry's tilt towards non-custodial wallets has been nothing short of revolutionary. By eliminating the intermediary, these wallets not only enhance security but also reinforce the decentralization that blockchain technology was built upon.
The shift has prompted a renaissance in wallet design, prioritizing user experience and security. The result is a landscape where users are not only participants but also their own bank, with the freedom and responsibility that self-custody entails.
In conclusion, the movement towards self-custody is a testament to the resilience of the blockchain community and its commitment to the principles of autonomy and self-governance.
As this trend continues, we can expect further innovations in wallet technology, with a focus on security, usability, and integration with the burgeoning decentralized finance (DeFi) ecosystem.
The cornerstone of any blockchain system is its wallet infrastructure, a critical component that has undergone significant evolution to meet the growing demands of users.
From simple storage solutions to complex financial tools, wallets have transformed into the gateway to the decentralized economy.
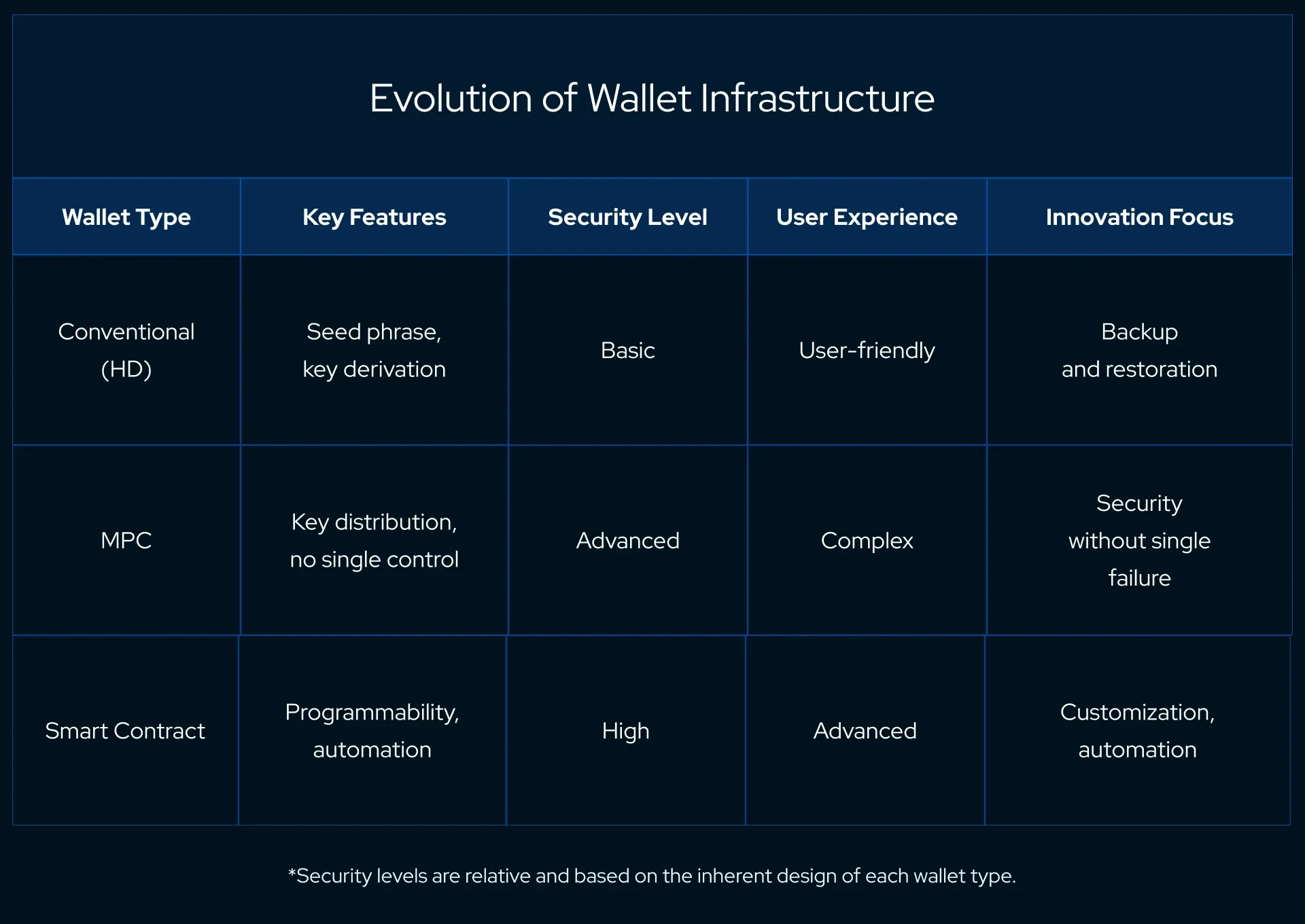
Conventional wallets, or Hierarchical Deterministic (HD) wallets, are the first generation of crypto wallets, offering a straightforward approach to key management.
They generate a seed phrase—a series of words that can regenerate all associated private keys and addresses. This innovation made it easier for users to back up and restore their wallets, but it still relied heavily on the user's ability to secure and manage their seed phrase.
Multi-Party Computation (MPC) represents a leap forward in wallet technology, focusing on enhancing security without compromising on usability.
MPC wallets distribute the responsibility of key management across multiple parties, ensuring that no single entity has complete control over the assets. This approach significantly reduces the risk of asset theft or loss due to a single point of failure.
Smart contract wallets, on the other hand, introduce programmability and automation to the wallet infrastructure.
These wallets are themselves smart contracts on the blockchain, enabling features like:
The need for improved security, a better user experience, and greater functionality is driving further evolution of wallet infrastructure as the cryptocurrency ecosystem matures.
Conventional wallets laid the groundwork, MPC wallets added a layer of distributed security, and smart contract wallets have brought a new level of sophistication to asset management on the blockchain.
The trajectory of wallet infrastructure development mirrors the growth of blockchain technology itself—from a novel way to store value to a comprehensive system for managing digital assets in a decentralized world.
With the introduction of MPC and smart contract wallets, we are witnessing a new era where security, autonomy, and programmability coalesce to form the future of digital asset management.
In the world of blockchain, key management stands as the bulwark against unauthorized access to crypto assets.
It embodies a complex interplay between security, user experience, and cost—factors that must be carefully balanced to ensure both the safety of assets and the accessibility of the blockchain ecosystem.
Security is paramount in key management, as the keys are the ultimate access to one's digital wealth. However, high security often comes at the cost of user experience, which can deter mainstream adoption.
Conversely, a focus on a seamless user experience must not compromise security. The cost factor also plays a crucial role; while robust security measures can be expensive, they’re essential for protecting investments.
Wallet providers must therefore strike a delicate balance, offering secure, user-friendly, and cost-effective solutions.
Managing private keys is a significant challenge for users across the spectrum, from novices to experienced traders.
The fundamental issue lies in the dichotomy of control and responsibility: maintaining total control over one's private keys means bearing the full weight of their security.
The failures of centralized exchanges serve as evidence that improper management or loss of keys can result in the irreparable loss of assets while entrusting them to a third party carries its risks.
The industry has responded with various solutions to address these challenges:
Hardware Wallets: Provide robust security by storing keys offline, away from online vulnerabilities. This includes technologies such as Trexor and Ledger.
Software Wallets: Offer convenience and easier access while incorporating various security features, for example, a Coinbase wallet.
MPC Wallets: Distribute key management responsibilities among multiple parties to mitigate the risk of a single point of failure.
Smart Contract Wallets: Enhance security through programmable conditions for transactions, reducing the risk of theft or unauthorized access.
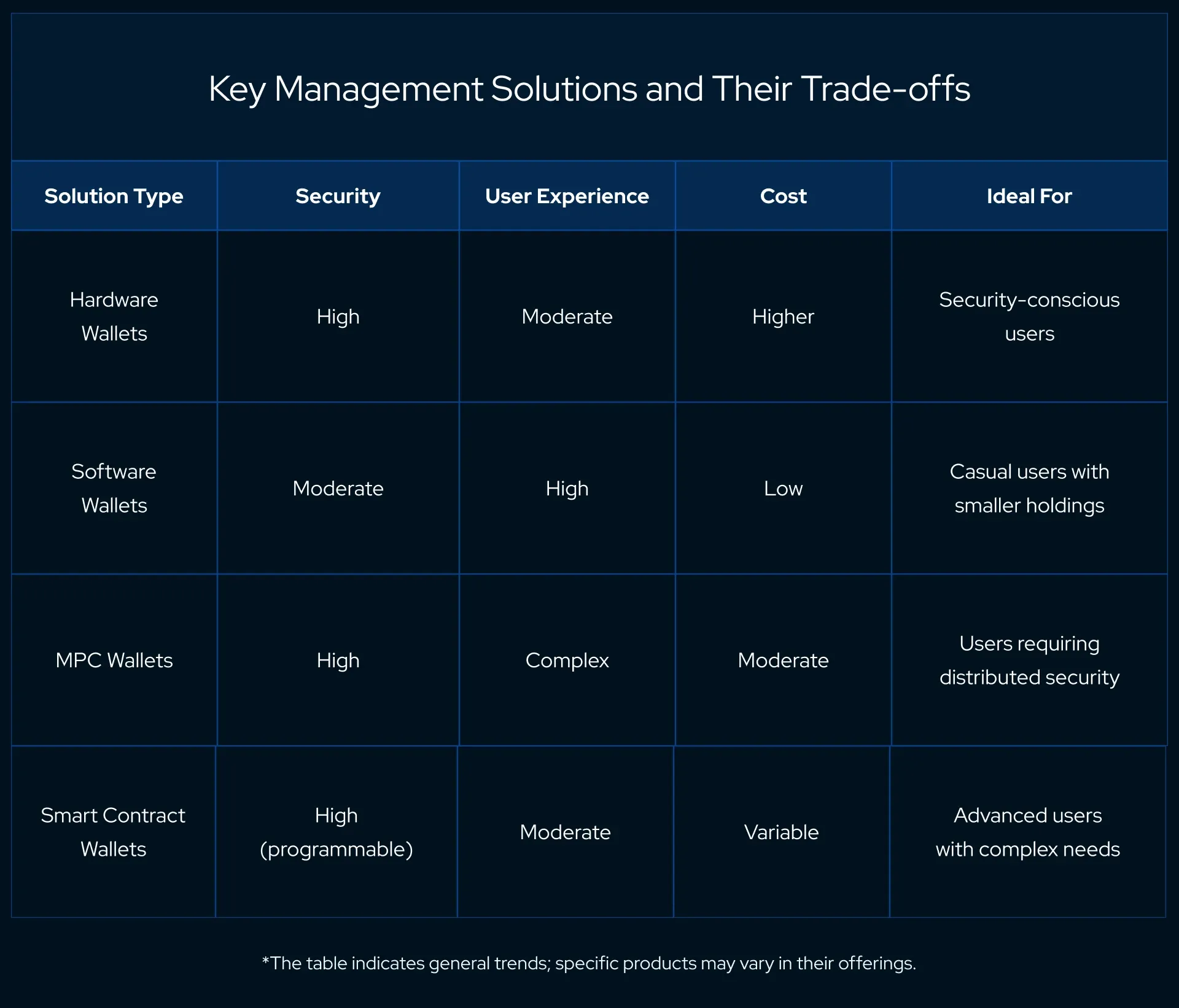
The evolution of key management solutions reflects the growing sophistication of the blockchain industry. As users demand more secure, convenient, and cost-effective ways to manage their keys, the market continues to innovate, offering a diverse array of wallets to suit different needs and risk profiles.
In conclusion, key management is a fundamental aspect of the blockchain user experience.
The industry's response to its challenges centered on the development of a suite of tools that cater to a wide array of preferences, balancing the triad of security, experience, and cost. As blockchain technology continues to evolve, so too will the solutions designed to keep our digital assets safe.
In the cryptographic arena of blockchain, conventional Hierarchical Deterministic (HD) wallets have long been the standard for managing digital assets.
They’re the foundation upon which cryptocurrency storage was built, yet they come with intrinsic limitations that the community has been working to address.
HD wallets generate a master seed, usually in the form of a mnemonic phrase, from which a tree of key pairs can be deterministically regenerated.
This seed phrase is a string of words that allows users to easily back up and restore their wallets without the need to save all the individual private keys generated for different addresses.
This deterministic structure provides a streamlined approach to wallet recovery and management, simplifying the user experience significantly.
Despite the convenience, HD wallets come with several limitations. The very feature that makes them user-friendly—the seed phrase—also creates a vulnerability.
If the seed phrase is exposed, all associated funds can be compromised. This represents a single point of failure that can lead to total asset loss.
Moreover, as all keys are derived from a single seed, if the algorithmic generation process is somehow compromised, it could lead to potential vulnerabilities across all generated addresses.
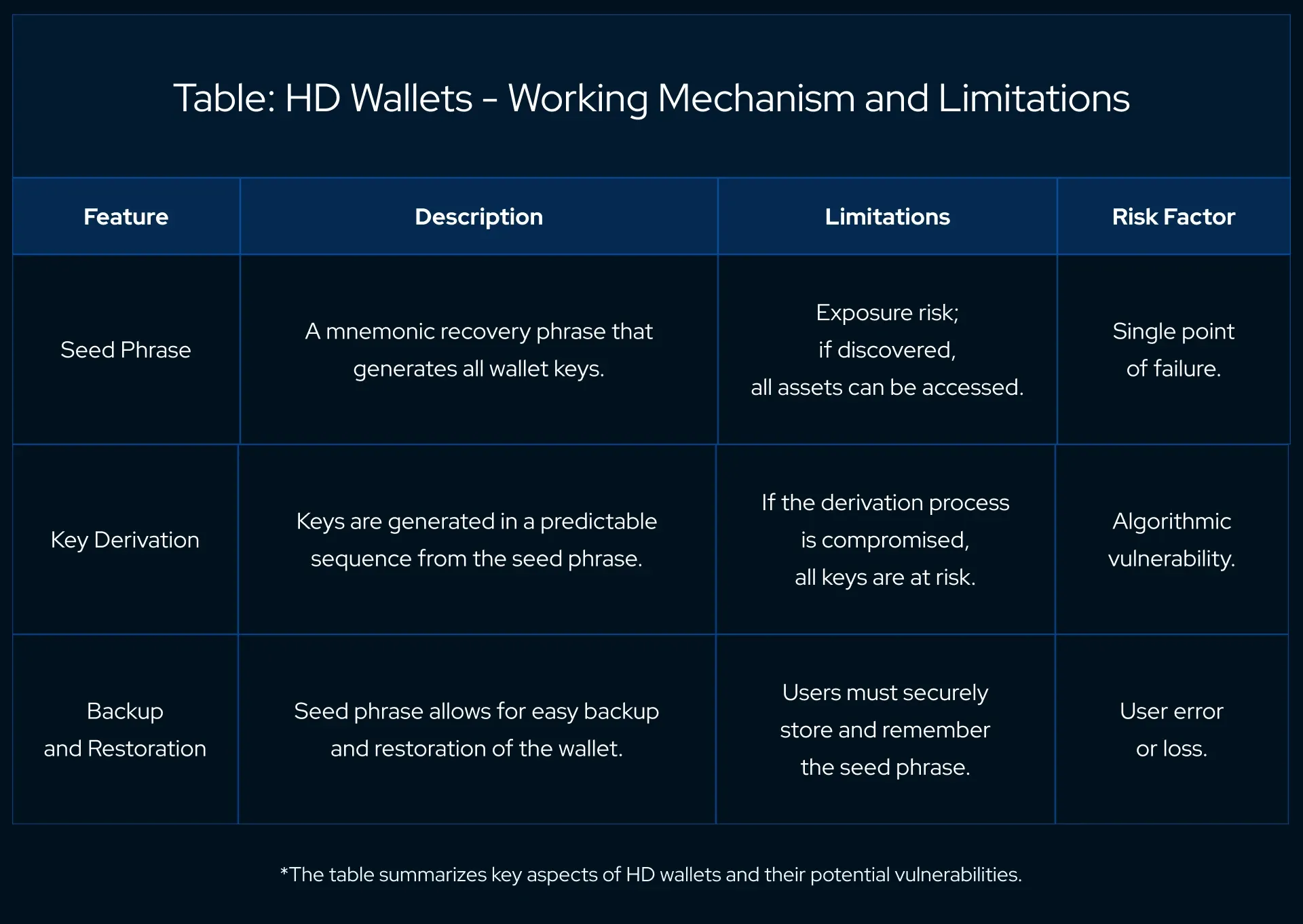
The single point of failure inherent in HD wallets has prompted the development of more advanced security measures within the cryptocurrency space.
While HD wallets continue to serve as a valuable tool for many users, the community's growing awareness of security has led to the adoption of more sophisticated solutions, such as:
Every innovation aims to distribute risk and add layers of security, ensuring users' assets are as safe as the keys that protect them.

The continuous evolution of digital asset security has given rise to Multi-Party Computation (MPC) wallets, a technology that is reshaping the concept of cryptographic key management by leveraging the power of collective assurance.
MPC technology is predicated on the principle that by dividing the responsibility of key management across multiple parties, the security of digital assets can be significantly enhanced.
In an MPC wallet, the private key is never whole at any one point. Instead, it’s split into multiple unique parts, with separate parties holding a fragment.
To initiate a transaction, a consensus among a subset of these parties is required, each contributing their segment of the key in a secure computation that results in the final signature.
This process ensures that no single party can act unilaterally, thus eliminating the single point of failure that plagues conventional wallets.
MPC wallets offer a robust security model by distributing trust among multiple entities, reducing the risk of asset theft or loss.
Moreover, they enable more flexible and dynamic control over transactions, including the ability to set up complex signing policies that can evolve as an organization's needs change.
However, the complexity of MPC technology can be a double-edged sword. On one hand, it provides enhanced security and policy enforcement, but on the other, it may introduce operational complexity and a need for coordination among the parties involved, which can be a logistical hurdle.
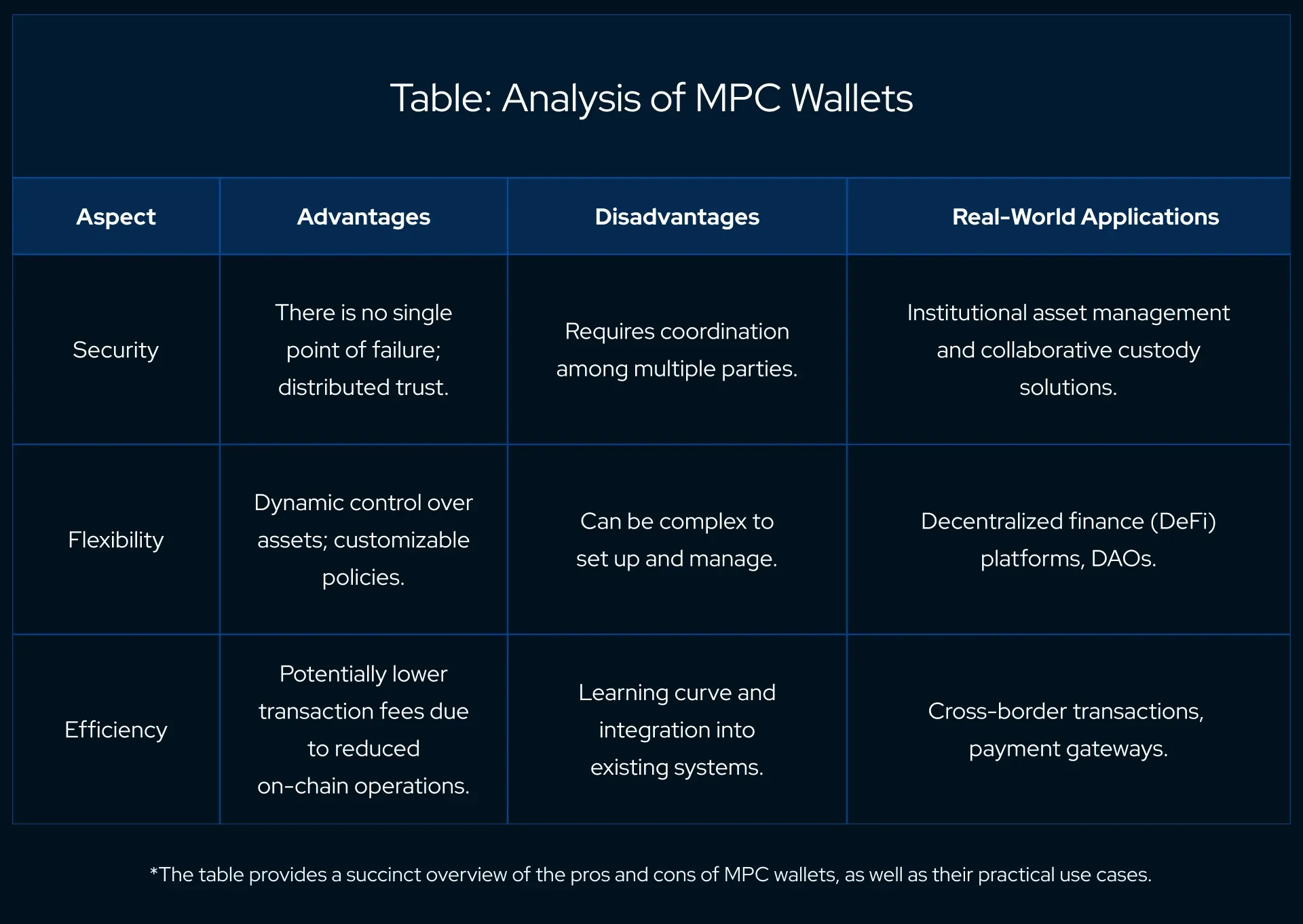
In the real world, MPC wallets are gaining traction in areas where security and distributed governance are paramount.
Institutional investors and financial services that require a high degree of auditability and control over transactions are increasingly adopting MPC solutions.
Similarly, decentralized autonomous organizations (DAOs), which operate on a principle of distributed control, are leveraging MPC wallets to manage their treasuries and enforce collective decision-making processes.
The growth of MPC wallets is indicative of a broader trend towards more secure and sophisticated key management solutions in the blockchain space. As the technology matures and its integration becomes more streamlined, MPC wallets are poised to become a mainstay in the arsenal of tools for secure digital asset management.
In the ever-evolving landscape of cryptocurrency, smart contract wallets have emerged as a transformative solution, redefining the capabilities and expectations of what a wallet can be.
Smart contract wallets diverge significantly from their conventional counterparts by utilizing the programmable capabilities of smart contracts on blockchain platforms like Ethereum.
Unlike conventional wallets that rely on a single private key for security, smart contract wallets operate as decentralized applications with logic that dictates how funds can be accessed and used.
This programmability introduces layers of customizable security features that can adapt to the complex needs of modern users.
The benefits of smart contract wallets are manifold. They offer enhanced security features, such as multi-signature transactions, spending limits, and recovery options that are not possible with traditional wallets.
Additionally, they can interact directly with decentralized applications (dApps), automate transactions, and integrate into the broader DeFi ecosystem.
However, the sophistication of smart contract wallets can also be their limitation. The code that governs them, while powerful, can introduce risks if not audited thoroughly, as bugs or vulnerabilities in the code could be exploited.
Moreover, the on-chain nature of these wallets often results in higher transaction fees compared to off-chain key signing.
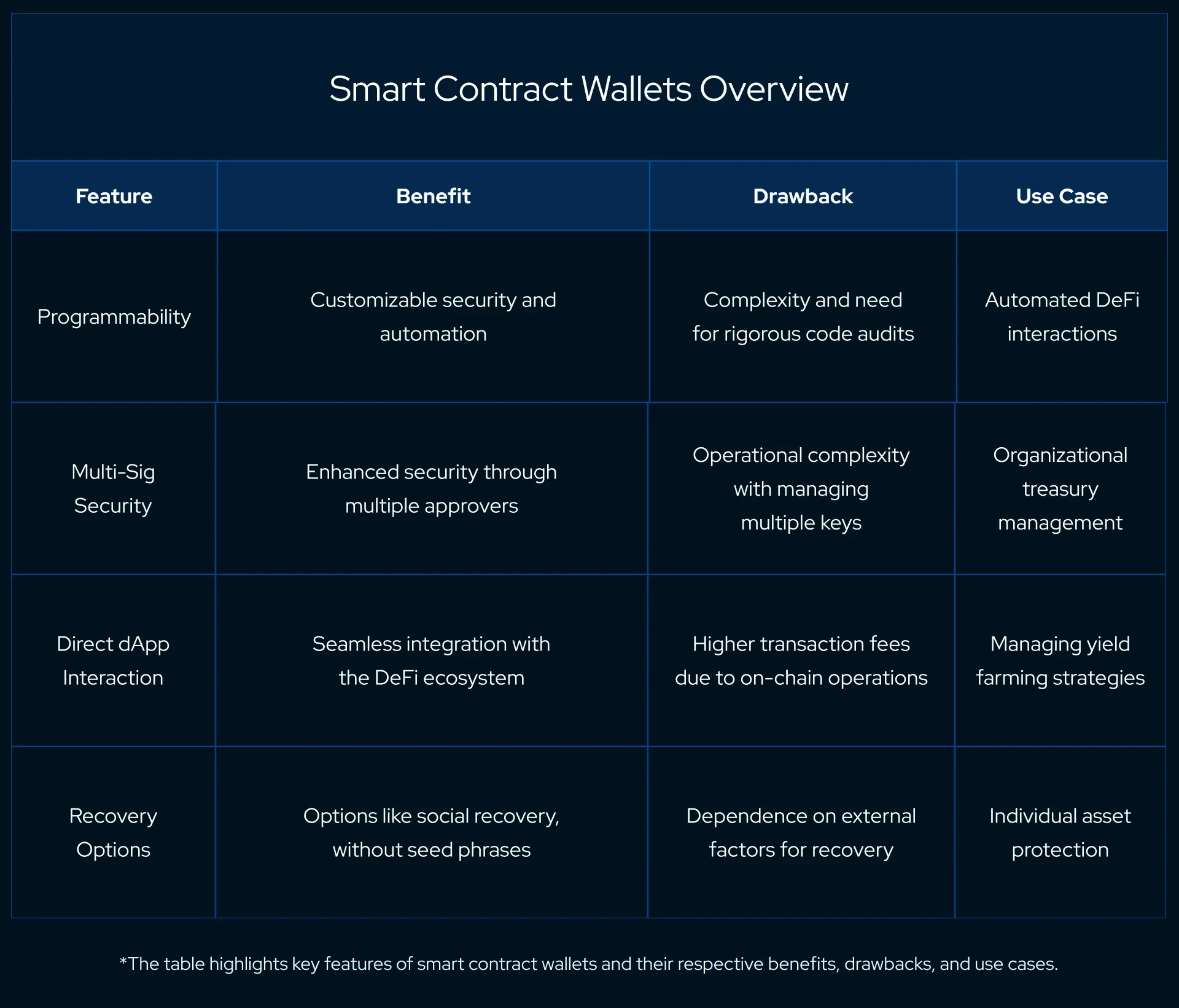
Smart contract wallets are being adopted for a variety of use cases that leverage their unique properties. Individuals use them to engage with dApps without leaving the security of their wallet environment.
Organizations appreciate the ability to set up complex treasury management protocols, such as requiring multiple team members to sign off on transactions, which enhances corporate governance and security.
Current trends also show a growing inclination toward integrating smart contract wallets with various sectors of the DeFi ecosystem, including automated trading, lending platforms, and insurance protocols.
This integration allows for a seamless user experience, where the wallet not only stores value but also actively participates in financial activities.
Smart contract wallets are at the forefront of the next wave of blockchain innovation. They provide users with unprecedented control and security, leveraging the full potential of smart contract technology.
As the blockchain space matures, these wallets are set to redefine the standards for asset management, transaction security, and user autonomy.
The continued growth and development of smart contract wallets will likely play a pivotal role in the mass adoption of blockchain technology.
In the world of cryptocurrency, wallet security is a paramount concern. With the rise in digital asset value, wallets have become prime targets for malicious actors.
This section explores the landscape of wallet security, focusing on high-profile exploits and the insidious nature of social engineering attacks.
The cryptocurrency industry has witnessed several high-profile security breaches, each causing significant financial losses and eroding trust in digital asset platforms.
These incidents range from direct attacks on wallet software to exploits in the broader infrastructure of the blockchain. For instance, the infamous Mt. Gox hack and the more recent Poly Network exploit serve as stark reminders of the vulnerabilities that exist within digital wallet security.
The consequences of such exploits are far-reaching. They not only result in the immediate financial loss of stolen assets but also have a lasting impact on investor confidence. This leads to heightened scrutiny from regulators and a push for more secure wallet technologies.
Social engineering attacks represent a different yet equally dangerous threat to wallet security.
These attacks exploit human psychology rather than technical vulnerabilities, tricking users into divulging sensitive information like private keys or seed phrases. Attackers frequently employ phishing attacks, impersonation scams, and fake wallet applications.
The effectiveness of social engineering lies in its direct appeal to human error, making it a challenging problem to solve with technology alone. Educating users about safe practices and the importance of vigilance remains a crucial component in combating these types of attacks.

The challenge of wallet security is an ongoing battle, requiring continuous vigilance and adaptation. As the methods of attackers evolve, so too must the defenses of wallet providers and users.
The industry's response has been multi-faceted, involving technological advancements, regulatory frameworks, and user education.
The future of wallet security lies in a combined approach that addresses both technical vulnerabilities and human factors, ensuring a safe and trustworthy environment for managing digital assets.
Account Abstraction represents a significant paradigm shift in how users interact with blockchain networks. It's a concept that blurs the traditional lines between contract accounts and external accounts, aiming to simplify and enhance the user experience.
Traditionally, blockchain networks like Ethereum have two types of accounts: Externally Owned Accounts (EOAs) that are controlled by private keys, and contract accounts controlled by code.
Account abstraction proposes to treat all accounts as smart contracts, enabling more flexible and user-friendly functionalities.
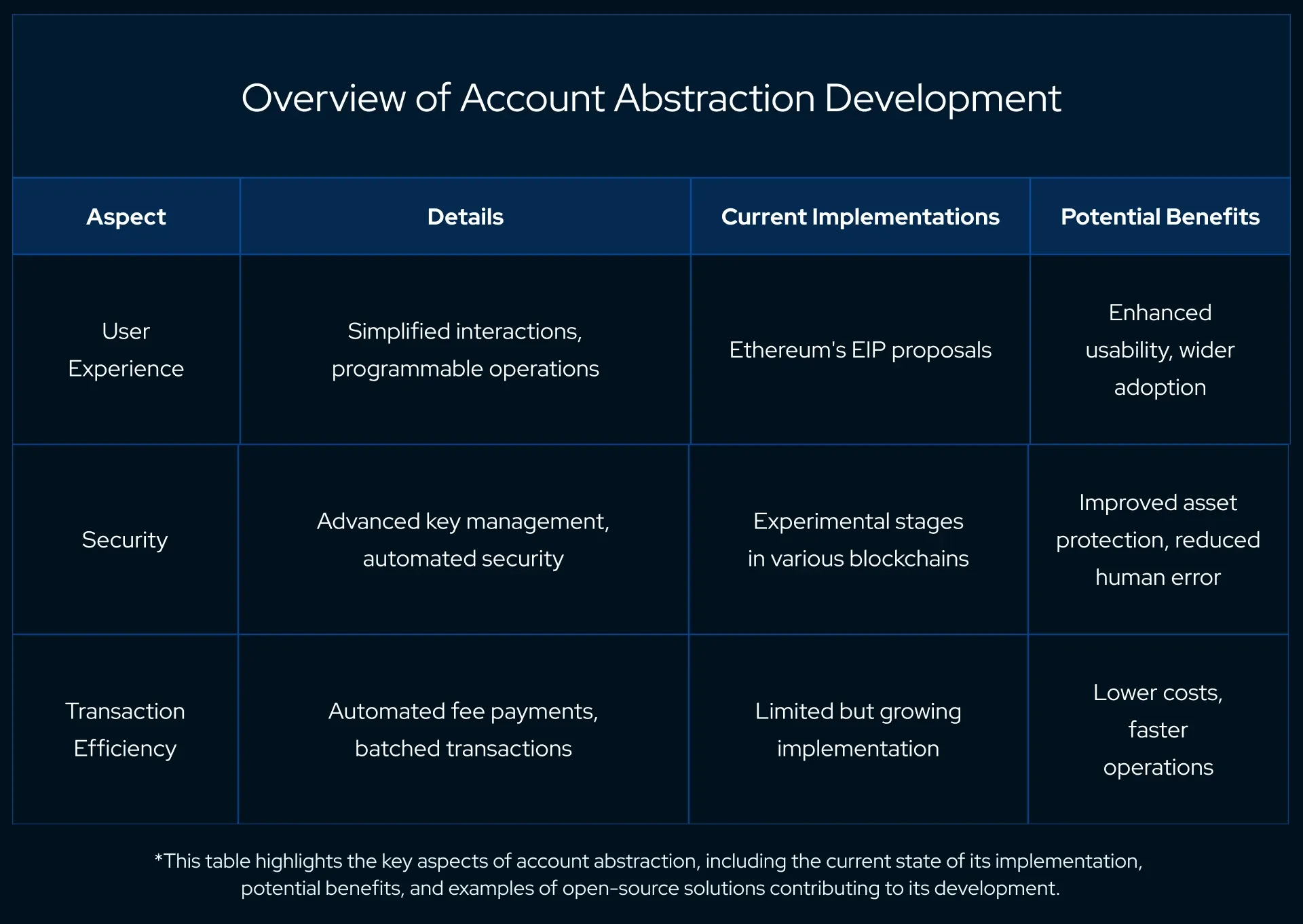
This approach would allow users to interact with blockchain applications more intuitively, with operations like transaction signing and fee payment being programmable and potentially automated.
While still in its developmental stages, account abstraction is showing promising potential across various blockchain platforms.
Ethereum, for example, has put forward several Ethereum Improvement Proposals (EIPs) to integrate account abstraction into its system.
These proposals aim to simplify user interactions, enhance security with more flexible key management, and even potentially reduce transaction costs through batching.
The potential of account abstraction lies in its ability to make blockchain and crypto transactions as user-friendly as traditional banking applications, all the while maintaining the security and decentralization that blockchains offer.
This could lead to broader adoption of blockchain technology, especially among users who are currently intimidated by the complexity of managing private keys and interacting with decentralized applications (dApps).
The development of account abstraction is powered by various open-source initiatives ensuring transparency and community-driven innovation.
These projects are crucial for testing, refining, and implementing account abstraction in a way that is accessible and beneficial to the wider blockchain community.
Account abstraction is poised to revolutionize the way users interact with blockchain networks, making them more accessible, secure, and efficient.
As this concept continues to evolve, driven by the contributions of the open-source community and advancements in blockchain technology, it promises to make decentralized platforms more user-friendly and accessible to a broader audience.
The ongoing research and development in this area signal a future where the complexities of blockchain interactions are abstracted away, paving the way for seamless integration into everyday digital life.
In the world of blockchain, transaction fees play a crucial role in network maintenance and user experience.
This segment delves into the intricate economics of these fees, their impact on users, the emerging concept of relayers and gasless transactions, and provides example calculations of potential transaction costs.
The underlying consensus mechanism, network congestion, transaction complexity, and other factors all affect transaction fees in blockchain networks like Ethereum.
These fees are essential for compensating miners or validators who maintain the network's security and integrity. However, high transaction fees can be a significant barrier, especially for small-scale transactions or during periods of high network congestion.
For users, this means balancing the need for quick confirmations with the cost of transactions. In times of peak demand, users might face exorbitantly high fees, impacting the feasibility of executing transactions, particularly for those in decentralized finance (DeFi) or regular small transactions.
To address the challenges of high and unpredictable fees, the concept of relayers and gasless transactions has emerged.
Relayers are entities that facilitate transactions on behalf of users and cover the initial gas costs.
They typically work within specific frameworks where the transaction costs are either subsidized or later reimbursed by the user in a different form, often a token specific to the platform or application.
Gasless transactions, often facilitated by relayers, are a user-friendly approach to blockchain interactions, removing the immediate burden of gas fees from the user.
This system is particularly beneficial for new or casual users who may not hold the native cryptocurrency of the network but still wish to interact with dApps or execute transactions.
To understand the economics of transaction fees better, let's consider a typical scenario on the Ethereum network.

Example calculation extracted on January 30, 2024, 11.00 GMT.
As you can see, using Relayer reduces the fees by 8-12%.
With the development of scalability solutions like Layer 2 networks and Ethereum's transition to Proof of Stake, transaction costs are expected to become more predictable and user-friendly.
Moreover, innovations like relayers and gasless transactions are making blockchain interactions more accessible, marking a significant step towards wider adoption.
As the blockchain landscape continues to mature, the interplay between Multi-Party Computation (MPC) wallets and smart contract wallets is crafting a new narrative of empowerment and security.
These innovative technologies are not in competition; rather, they complement each other, each addressing different needs within the ecosystem.
MPC wallets offer a decentralized approach to security, dispersing the risk and responsibility of key management. They provide an environment where trust is shared and no single entity can compromise the system.
Smart contract wallets, conversely, bring programmability and flexibility to the forefront, allowing users to set rules and conditions that govern their funds.
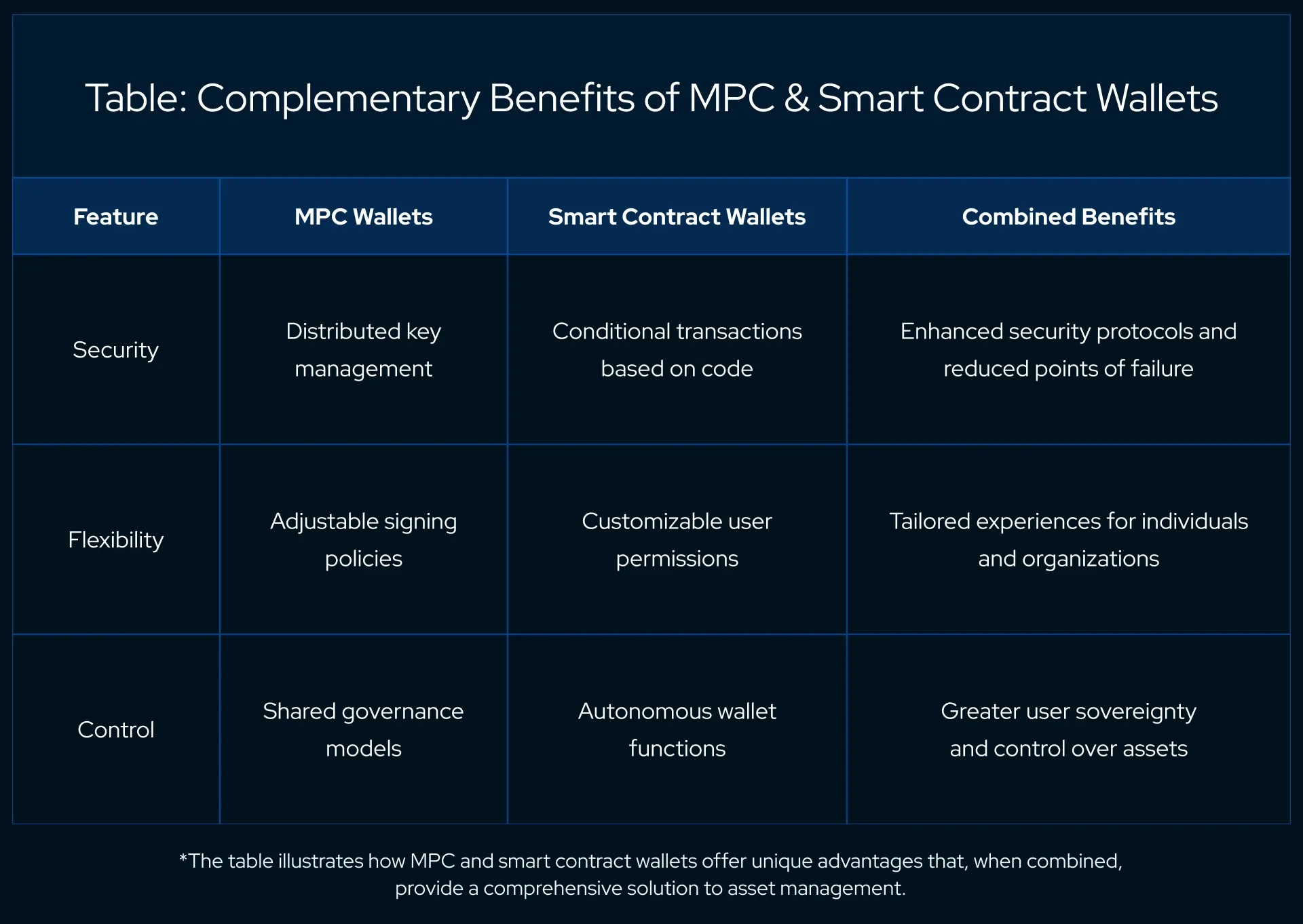
The ascent of decentralized finance (DeFi) underscores the demand for self-sovereignty over financial transactions. Users are seeking platforms that offer security and autonomy without the need for intermediaries.
MPC and smart contract wallets are pivotal to this movement, providing the tools for users to engage with DeFi products confidently and securely.
Looking forward, the future of wallet infrastructure is poised to become more intuitive, secure, and integrated with the broader blockchain ecosystem.
Innovations like account abstraction are set to simplify interactions, making them more approachable for the average user.
As the industry gravitates towards solutions that offer both security and ease of use, wallet technology will continue to be at the forefront, evolving to meet the demands of a growing and diverse user base.
The convergence of MPC and smart contract wallets is guiding the blockchain community toward a future where financial self-sovereignty is the norm.
This journey towards decentralization is not just a technological evolution—it's a cultural shift that places users in the driver's seat, giving them complete control over their digital assets.
With continued innovation and user-centric design, wallet infrastructure will remain a cornerstone of blockchain's promise to deliver a decentralized, secure, and accessible financial future.
